Ssh Config Password
Used for ssh or scp or anything that needs SSH secure access.
Quick reminder...
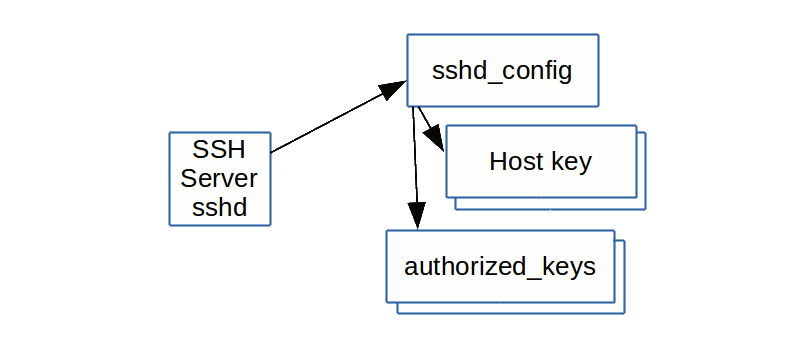
The ssh-agent is a helper program that keeps track of user's identity keys and their passphrases. The agent can then use the keys to log into other servers without having the user type in a password or passphrase again. This implements a form of single sign-on (SSO). The SSH agent is used for SSH public key authentication. Some server providers, such as Amazon EC2 and Google Compute Engine, disable SSH password authentication by default. That is, you can only log in over SSH using public key authentication. SFTP is a protocol that runs over SSH, so this means SFTP using passwords will not work by default when SSH password authentication is disabled. I'm looking for a way to disable SSH clients from accessing the password prompt as noted here. I am unable to disable the password: prompt for root login. I have change the sshdconfig file to rea. The SSH protocol (aka Secure Shell) is used to establish secure and reliable communications between two hosts. It supports different ssh authentication methods and uses strong encryption to protect exchanged data. It is possible to use SSH-based communications instead of clear-text remote CLI protocols (telnet, rlogin) and unencrypted file. We configure single sign on using GSSAPI Authentication, so that we can login on one RHEL host and use ssh to connect to another RHEL host, without typing our passwords or use ssh keys. This requires that your Linux host is connected to Windows Active Directory or IPA Server. Further you can setup SSH to configure kerberos authentication.
If you've done it before but forgot, here's the refresher. (Otherwise, read below.)
On server:
On client:
Test it:
Password In Ssh Config File
Background
It's common to use ssh and scp for communicating and transferring files to and from a server. If you want to auto-login without a password, here's how to setup SSH to use encryption keys to do so.
On the Server
Use ssh to login to your server under the account name you want to use.
Run ssh-keygen to create an encryption key pair, the public and private keys. You can just hit return for each question.
CD to the .ssh dir and list the files to understand what you've got:
Add the public key id_rsa.pub to the SSH authorized_keys file. Be sure to use the >> to append it to any other keys you might have:
Be sure the file is hidden from other users, and you can delete the public key now.
On the Client
Log-off the server, so you're back on the client. Enter your .ssh directory and download the id_rsa file (the private key) from the server to your local machine:
Try it out:
And you can use scp for secure file transfer:
Multiple SSH keys

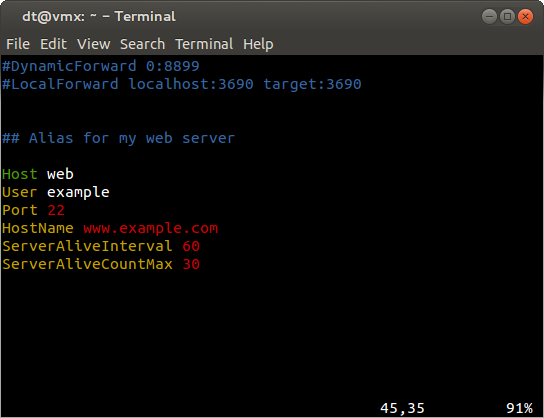
If you login to more than one server, you can configure SSH to fetch the correct key. Here's an example of adding to the ssh config file:
If you need a different username on your server, you can add:
Ssh Config Password

SSH Agent
You can setup an environment variable to make it possible for programs that use SSH to find your keys, avoiding the requirement than you enter your passphrase each time.
Insert some lines like this into your .bash_profile:
